Monday, January 16, 2012
Simple math and CSS are
used to create the below heat map showing the results of the All Our Ideas Wikipedia
Banner Challenge.
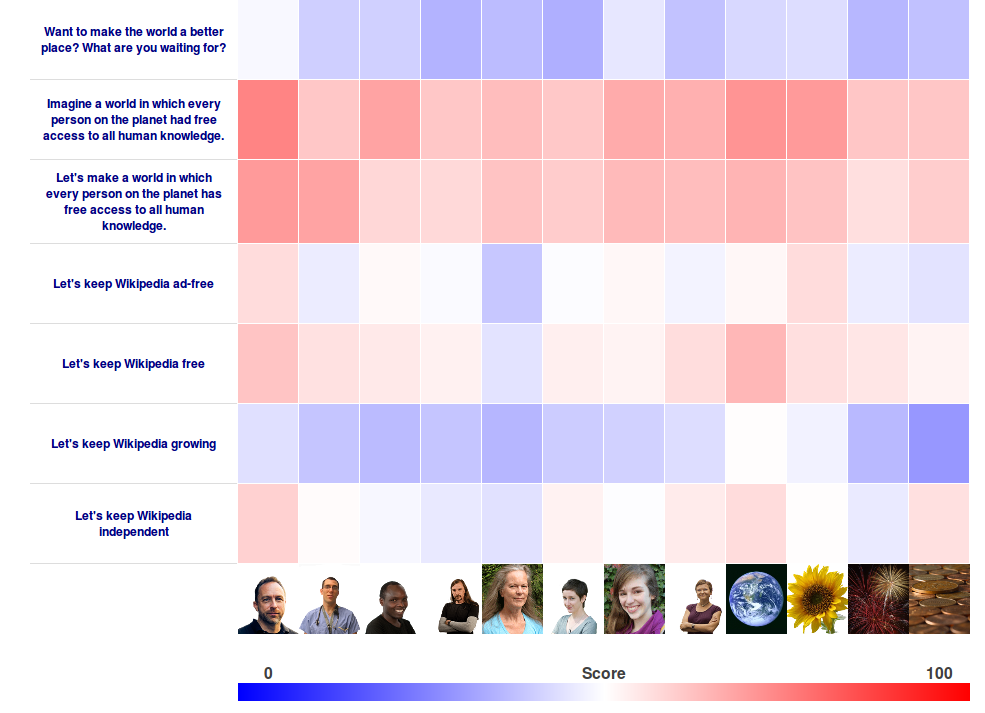
Pairwise data collection is particularly suited to matrix based
visualization. We use intuitive colors so that after quickly skimming the
results your gaze naturally drifts towards the better and worse banner
pairs.
Monday, August 29, 2011
This presentation concerns a method I developed to use user interactions
with search results to automatically re-rank results and thereby produce a
higher-quality ranking, which increases in quality with more user interaction.
Below is a presentation showing the method and results:
Download the above presentation
and the complete thesis.
Friday, August 26, 2011
I will be defending my thesis, Learning to Rank from Relevance
Feedback, Monday August 29th at 1500 in room G.005 at Science
Park.
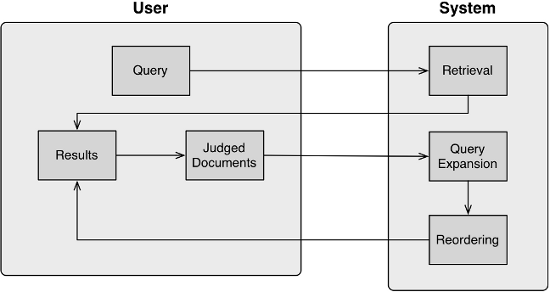
Below is a schematic of the method I developed to learn and re-rank documents
as users browse through them:
The abstract of my thesis is below. I will post the full text next
week.
When searches involve ambiguous terms, require the retrieval of many documents, or are conducted in multiple interactions with the search system, user feedback is especially useful for improving search results. To address these common scenarios we design a search system that uses novel methods to learn from the user's relevance judgements of documents returned for their search. By combining the traditional method of query expansion with learning to rank, our search system uses the interactive nature of search to improve result ordering, even when there are only a small number of judged documents. We present experimental results indicating that our learning to rank method improves result ordering beyond that achievable when using solely query expansion.
Sunday, June 05, 2011
The Helioid team and collaborators have released a Europe
Travel Guide for Android.
We have packed over
3600 European destinations in a tiny offline guide. It is filled with
great content from wikitravel and is the perfect guide for
backpackers.

- Up-to-date info about transport and accommodation options
- Hundreds of helpful phone numbers, email addresses, and URLs
- Dining and shopping guides for major cities
- Country-specific safety and emergency contact information
- Extensive information about local culture and customs
Available on on
Android Market now.
Monday, May 16, 2011
Below are the slides from a presentation I gave
at the Natural Language Processing & Learning Workshop.
I presented my project for the Unsupervised Language Learning class,
entitled "Unsupervised Constituency Grammar Induction: Learning Bracketing and
Phrasal Categories."


